
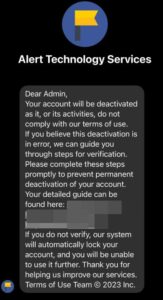
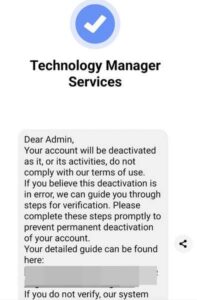
Have you ever received messages on Facebook claiming to be from Meta’s Business Help Centre? Unfortunately, scammers are targeting small businesses and creators with phishing attempts, aiming to steal account access. Let’s dive into how these scammers operate and how you can protect yourself.
Understanding the Scam
The Meta Business Help Center phishing scam preys on Facebook and Instagram business account owners. Scammers send urgent messages, pretending to be from Meta’s real help teams, alleging policy violations that could lead to permanent page deletion.
These messages create a sense of urgency, stating that the recipient has 24 hours to fix the issues by clicking on provided links to submit account reviews. However, these links lead to fake login portals designed to capture your credentials, giving scammers access to your account.
Once they gain access, scammers can wreak havoc on your brand by impersonating your identity, stealing valuable audience data, running fraudulent ads, demanding ransoms, and more.
Delivery Strategies
These phishing messages can reach you through various channels, including Facebook Messages, email notifications, and text messages. They often spoof verified sender details to appear legitimate, using Meta’s logos and Business Help Center channel name.
Facebook Messages: Direct alerts to account inboxes pretending to be from Meta’s verified Business Help Center.
Email Notifications: Messages containing Facebook branding and official warning formats are sent to account emails on file, often using “Critical Account Alert” subject lines to entice opening.
Text Messages: SMS texts sent to linked mobile numbers pretending to be from Meta support teams, identifying recipients by name and citing removal justifications to seem credible.
How the Scam Works
The scam starts with an unsolicited message, claiming to be from Meta’s Business Help Center, warning about policy violations and urging immediate action. The message includes a link to an official-looking account review portal, which is actually a phishing site designed to steal your login credentials.
Once they have your credentials, scammers can exploit your account in the following ways:
Impersonate Brands: Make posts contradicting company values after cultivating audience trust over years.
Hijack Followers: Message engaged customers redirecting them towards malicious links or fake promotions from formerly trusted profiles.
Steal Marketing Data: Access and sell valuable audience demographics and contact info to unscrupulous third-party advertisers.
Run Fake Ads: Place high-spending ads linking external financial scams, earning payouts from stolen payment methods.
Demand Ransoms: Further extort locked-out business owners desperate to salvage reputations built via social media.
Spotting the Scam
While these messages may seem urgent and convincing, there are subtle signs that can help you identify them as fraudulent:
1. Non-Specific Violation Details
Authentic warnings outline exact policy violations. Vague claims of “repeated violations” without proof indicate scam threats.
2. Inconsistent Sender Identity
Messages pretend to come from Meta’s real Business Help Center. Scrutinising sender details reveals spoofed verified badges and channel names.
3. Illogical Ultimatums
Meta allows reasonable response times to most account issues before considering permanent disabling. Scam threats impose unrealistic 24-48 hour deadlines counting down to termination.
4. Stylistic Language Irregularities
Professional messages avoid awkward phrasing or grammatical mistakes. Contrastingly, scam content contains spelling and/or grammatical errors exposing non-native English origins.
5. Suspicious Links
While incorporating Facebook’s name, scam site URLs lead to different domains lacking the SSL certificates securing legitimate Meta properties. Entering data on unencrypted pages enables credential theft.
What to Do If You’ve Fallen Victim
If you’ve entered your credentials into a suspicious message, follow these steps to secure your accounts:
Change Account Password
Reset the passwords for any accounts that were accessed by the scammers. This will lock them out. Enable enhanced login approvals (2-factor authentication such as SMS or email) for extra security against repeat intrusions.
Review Recent Activities
Check account posts, messages, payments and ads for unauthorised changes. Remove any fraudulent items falsely representing brands that followers rely on for legitimate guidance.
Run Antivirus Scans
Scan all personal and professional devices in case embedded malware granted backdoor access for future data harvesting or distribution schemes.
Warn Your Audience
Inform your audience about compromised profiles that communications should be cautiously verified until account security is restored. Apologise for the confusion while advising contacts to watch for potential misinformation-spreading scams during this time.
Report Incidents To Meta
File detailed reports to Meta regarding phishing attack specifics like links, source profiles and screenshots so investigations can disrupt these schemes at scale by banning fraudulent actors and domains.
Enhance Login Protections
For the most resilient defence, ensure multiple login approval methods that require secondary identity verification through prompts on new devices even after changing passwords. Remain vigilant about monitoring account activities for anything unusual in the weeks ahead.
Conclusion
By staying vigilant and following these steps, you can protect yourself and your business from falling victim to phishing scams. Remember to always verify the authenticity of messages before taking any action.
